Presenting Your Cloud Security Strategy to the Board
Presenting to the board can be nerve-wracking, even for seasoned executives. Focusing on why, how, and what will greatly increase your chance of success.
Your time slot is coming up fast. You have 15 minutes to present to the board. Over the past few quarters, you've noticed the questions other executives have received from board members have shifted from operational inquiries to instead expressing an appetite for risk and growth.
As you listen to other business leaders respond, you can't help but wonder if your story on controls and compliance is the right one to be telling. You begin to perspire as you realize that you are the Chief Brand Protector and Chief Digital Enablement Officer, despite having the title Chief Information Security Officer (or head of Cybersecurity). You now wish you had a strategy that wasn't controls and compliance focused. You realize what you really need is a growth and enablement story that includes these other things.
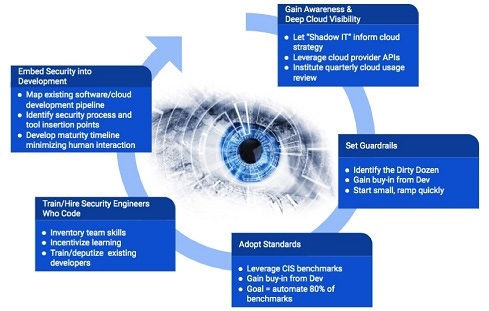
Back in 2019, which seems like an eternity given COVID-19, the Prisma Cloud team at Palo Alto Networks introduced a high-level framework for building a comprehensive cloud security strategy known affectionately as the Big Cloud 5. Since it was published, many security teams have utilized this to build the foundation of their cloud security strategy.
I've received many questions around putting this into a more business-focused context that board members and non-cyber executives can clearly understand. Let's jump into it.
Simon says start with why
Simon Sinek says that great leaders always start with the 'why.' The same should apply when presenting your cloud security strategy to the board. They will want to know why this strategy, how you will accomplish it, and what you will need to implement it.
Establishing the why is the clearest path to success. The trick is to get the board members nodding their heads because they see a tight relationship between your strategy and how it will enable the rest of the business to meet their goals.
You might start your presentation by saying something like, “Research shows that 65% of security incidents in the cloud are the result of customer-induced misconfigurations. I don't want us to be in that 65%. I've chosen to focus on the following five areas [see chart above] for 2021 because they will enable our business units to rapidly expand our cloud adoption and increase our speed to market. This will enable us to exceed our growth targets (be as specific as possible) while aggressively defending against threat actors. I want to walk you through a recent incident that made the headlines which illustrates why this strategy is important.”
With this opening statement, you've done a few key things. First, you didn't make a statement based upon conjecture. You started with a fact that they likely were not aware of. This means you've already added value. Remember, when talking to executives and/or board members, you are trading time for value. They all have limited time, so always aim to bring massive value.
Second, you are painting a vivid picture of how security is a business enabler and that you understand the bottom line of the business is the bottom line, not controls. Third, you've been clear that, while you understand the bottom line is critical, you are not painting a Pollyanna picture of the future when it comes to cyber threats. Lastly, you've piqued their interest with something they may have read about but may not have fully understood. This is an amazing opportunity to talk about an attack and break it down into plain English.
Depending on how much time you have to present your strategy, it is always important to clearly spell out how it will contribute to the bottom line and/or corporate goals. Below are some examples of cybersecurity benefits you might refine for your pitch (but don't use all of them). Always cite one or two specific activities for each one you do use.
Allows for rapid expansion of cloud services across the company, thereby reducing costs and improving speed to market.
Lets DevOps teams focus on their core competencies instead of trying to become security experts.
Removes the traditional security “roadblocks” that can slow cloud adoption and impact project delivery timelines.
Creates a pathway to rapidly enter new markets that previously had high barriers to entry due to strong compliance requirements (e.g., FedRAMP, China's Cyber Security Law (CSL), Australia's SCI Act).
Protects sensitive data in the cloud, thereby reducing potential impacts to customer data and our company's reputation.
Tell me how
"I asked you how to do it, and you told me what I should do ... I know what I need to do. I just don't know how to do it." -- Andy Grove, former Intel CEO
How you will accomplish your goal is very different from the vision you painted above in the why and what. When you answer the what, that is really just the tip of the iceberg. How gets into the gritty details.
I want to caution you, however, not to get too deep, or you risk losing the board's attention. Know your audience and your time slot.
Key items to call out include people, process, technology, and data. This means clearly spelling out which teams you see as key stakeholders, organizational processes that will be impacted, as well as technology that will underpin your plan.
While the board doesn't need to understand all the intricacies, they will be very interested in how you plan to track progress. I recommend coming up with a shortlist that focuses on both lead and lag measures. Lag measures focus on your progress towards achieving your stated goals. Metrics are most commonly lag measures. Lead measures, on the other hand, tell you if you are winning, and they are easier to influence.
Work with your team to develop a set of lead and lag metrics around the Big Cloud 5. There should be a set that you report up to the board (don’t overwhelm them), as well as another set that goes much deeper that you use within your team. As a fellow CISO of mine commented recently, “Don't make security the best-kept secret of the company. Make your metrics public.”
What you need
No presentation to the board is complete without clearly stating what you need to accomplish your vision and strategy. Your ask should be clear in terms of resources and timelines. Resources always boil down to money, and timelines should paint a realistic picture of how long you believe it will take to accomplish your stated objectives.
An effective technique is to verbalize what could happen if your strategy is not funded. This is about educating the board on the risks if they choose not to take the path you've recommended. When taking this approach, it's imperative to present a dispassionate view that includes peer feedback. Prior to the board meeting, give others time to shoot holes through your approach.

Have a peer review any arguments you may make.
At the end of the day, the board's job is to ensure wise decisions are made on behalf of the shareholders. This includes making sure corporate resources are being managed wisely. In order for them to make informed decisions, they need to understand the pros and cons. It is your job to present this information to them as objectively as possible.
It's all about focus
Presenting to the board can be nerve-wracking for even some of the most seasoned executives. Focusing on answering the three questions of why, how, and what will greatly increase your chance of success. Remember, while board members are likely to be extremely smart and experienced, they are not usually cybersecurity experts. Use your opportunity in front of them to build a relationship, add value, cast a clear vision, and show them how you will keep score with metrics.

Matt Chiodi has nearly two decades of security leadership experience and is currently the Chief Security Officer of Public Cloud at Palo Alto Networks. He is a frequent blogger and speaker at industry events such as RSA. He currently leads the Unit 42 Cloud Threat team, which is an elite group of security researchers exclusively focused on public cloud concerns. He is also on faculty at IANS Research.
[All graphics and images in this article are sourced from Palo Alto Networks]
About the Author(s)
You May Also Like
How to Amplify DevOps with DevSecOps
May 22, 2024Generative AI: Use Cases and Risks in 2024
May 29, 2024Smart Service Management
June 4, 2024







